WWDC 2022: How Apple Plans to Make True Single Sign-On a Reality
 Kandji Team
Kandji Team
For Mac admins, single sign-on (SSO) sounds like a great idea. In that ideal world, a user would turn on their Mac computer, sign in with their credentials, and then—with that one sign-in—have access to everything: their local user account; apps on their device; resources you provide on the local network; and apps and services that reside in the cloud.
So far, though, that ideal has remained out of reach. The user still has to sign in first to a local account, then again to apps and services. SSO services such as Okta and OneLogin make that easier, by providing a single login for cloud-based resources. But true single sign-on isn’t here yet.
It’s not for lack of trying on Apple’s part. A few years ago, with the release of macOS 10.15 Catalina and iOS and iPadOS 13, Apple introduced single sign-on extensions, which enabled users to authenticate to apps and services using the credentials they’d established with an identity provider (IdP). But even then, users had to sign in once to unlock the device, then sign in again to the extension. More importantly, for that to work, IdPs had to enable those extensions—and few did.
Judging by two of the announcements Apple made at this week’s Worldwide Developers Conference (WWDC), however, it’s clear that the company remains committed to making true single sign-on a reality.
Platform Single Sign-on
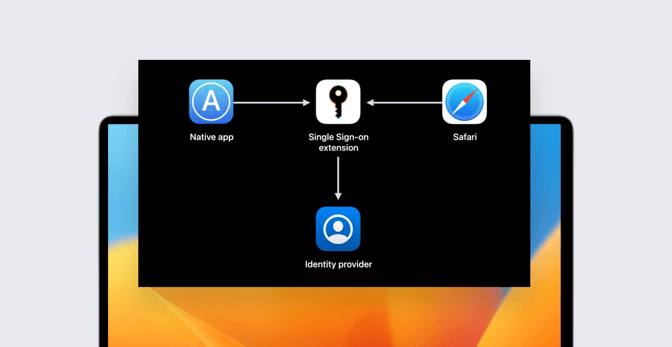
The first of these announcements was Platform Single Sign-on. In macOS 13 Ventura (slated to ship this fall), this framework will indeed allow users to sign in once at the login window and, in so doing, also be signed in to apps and websites that use the organization’s identity provider (IdP) for authentication.
The first login unlocks the local account (and, at the same time, FileVault encryption). After that, the user can use their IdP credentials for subsequent unlocks. The system supports authentication with a password or a Secure Enclave-backed key.
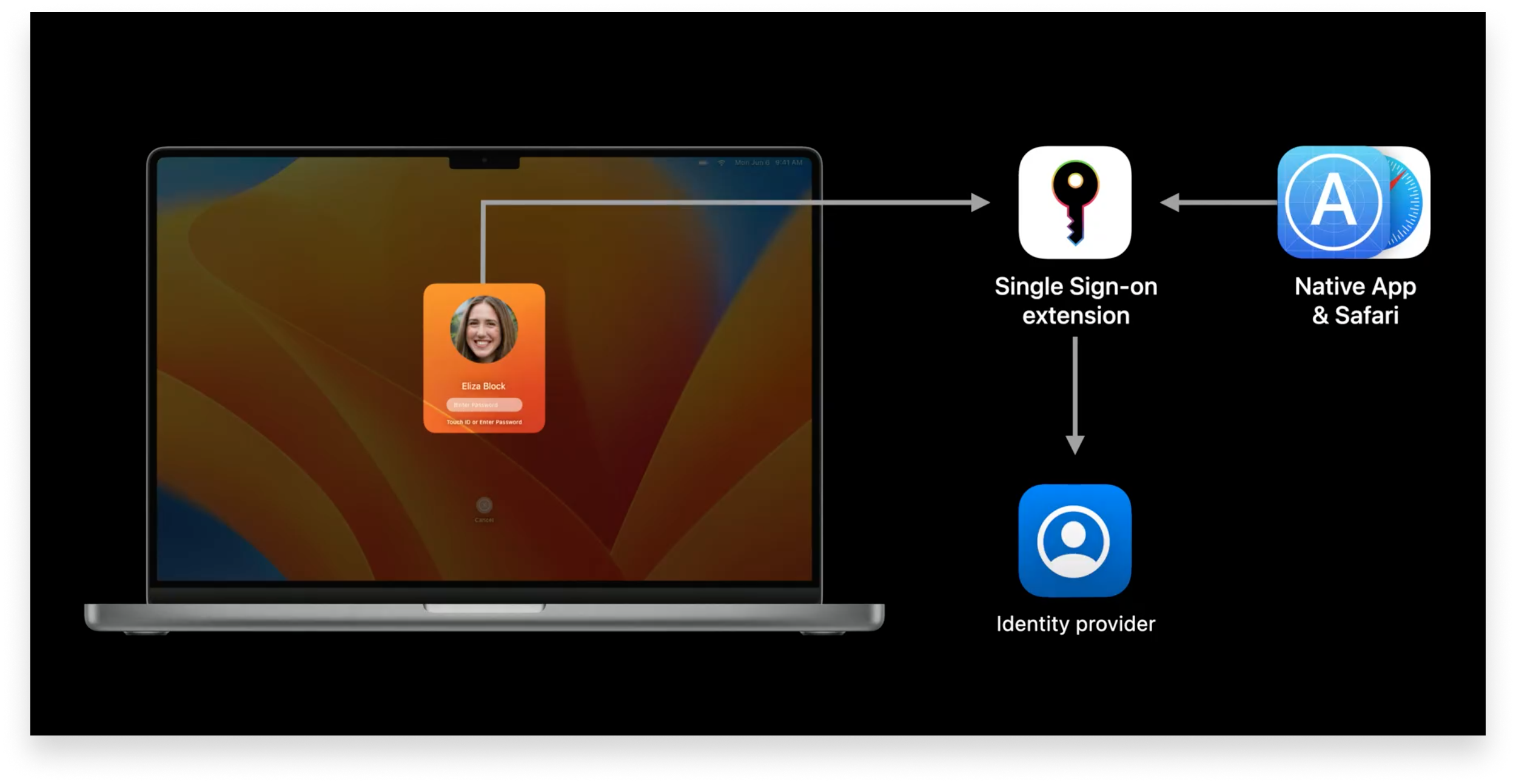
If the password changes at the IdP, Platform SSO will validate it during an unlock attempt. Platform SSO doesn’t check with the IdP on each unlock; it only does so when the user attempts to use a new password or to retrieve SSO tokens.
Those tokens are what make the system work: Acquired by the operating system from the IdP at login, they’re stored in the keychain and made available to third-party SSO extensions.
Note that platform SSO will not prevent access to the device based on the response from the IdP; for that, admins will need to use device management or some other workflow.
Apple said in its WWDC presentation that Platform SSO is a modern replacement for Active Directory binding and mobile accounts. As with previous SSO efforts, however, Platform SSO needs IdPs to implement the protocol and build the necessary extensions. And device management solutions will need to update their Extensible SSO profiles to support the protocol’s new keys.
Enrollment Single Sign-on
Apple is also introducing a form of single sign-on specifically for user enrollment. The company says it’s a way for personal devices both to enroll in MDM and to access apps and services, all with a single authentication.
Enrollment SSO is based on Apple’s extensible SSO and on account-driven user enrollment, which was introduced in iOS and iPadOS 15 and which allows users to enroll their own devices by signing in with a Managed Apple ID (specifically, by entering that ID in Settings > General > VPN & Device Management > Sign in with Apple).

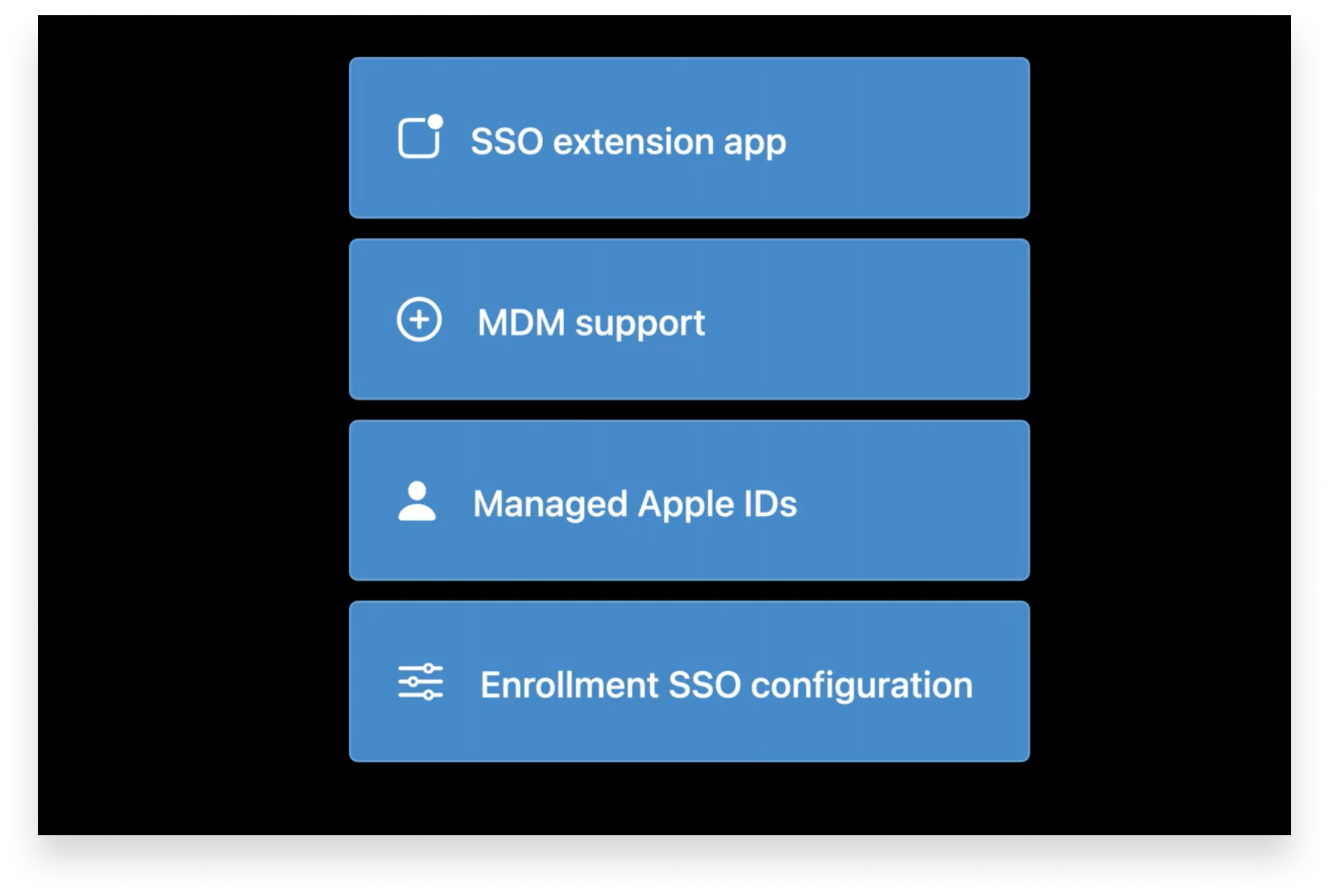
The workflow goes like this: After a user enters that ID in Settings, they’re prompted to download an enrollment app from the App Store. That app includes the Enrollment Single Sign-on extension and provides an interface for authentication. That app can be configured to use any authentication technology. The user signs in once; the app then continues through the enrollment workflow, without requiring the user to sign in again.
This all requires four components to be in place:
- The app that’s been configured to support enrollment SSO;
- A device management solution that’s been federated with an IdP;
- A Managed Apple ID set up in Apple Business Manager (or Apple School Manager); and
- An MDM server that’s been configured to return information the app needs to authenticate the user.
Enrollment single sign-on will initially be available in iOS and iPadOS 16.
Both Platform SSO and Enrollment SSO have their limitations and their own specific use-cases. But they also both have “SSO” in their names—an indication that Apple remains as committed as ever to making the dream of single sign-on a reality, even if that has to happen incrementally.
To learn more about Apple's new SSO moves, check out the video What's New in Managing Apple Devices (requires an Apple developer account).
About Kandji
Kandji remains committed to bringing the latest Apple technologies to life to make admins' lives easier and more productive. With powerful and time-saving features such as zero-touch deployment, one-click compliance templates, and plenty more, Kandji has everything you need to bring your Apple fleet into the modern workplace.