Manual Device Enrollment Now Results in macOS Supervision, New from WWDC 2020
 Kandji Team
Kandji Team
A lot of big news came out of the Worldwide Developers Conference (WWDC) 2020, including a new update for macOS Big Sur regarding device supervision, manual Device Enrollment, and User Approved MDM (UAMDM). Automated Device Enrollment (formerly DEP) used to be the only way to supervise your devices, but Apple’s latest update changes that.
In this post, we’re going to talk about how manual Device Enrollment with User Approved status now results in device supervision, what this means for IT administrators, and why Automated Device Enrollment is still important.
Here’s an overview:
- What’s Changing in Device Enrollment & Supervision with Big Sur?
- What are the Implications for IT?
- Why Automated Device Enrollment Still Matters
What’s Changing in Device Enrollment & Supervision?
At WWDC 2020, Apple announced that manual Device Enrollment with User Approved (UAMDM) status will now result in supervision on macOS Big Sur. Here, manual Device Enrollment refers to enrolling devices manually into MDM via an enrollment profile, while UAMDM refers to an enrollment status achieved when users enroll into MDM in an approved way or approve the MDM profile post enrollment. We’ll break each of these down in this section.
Before this change, there was only one route to supervision on macOS Big Sur: for any Mac device enrolled in Automated Device Enrollment (DEP), supervision was automatically enabled.
Now, a new route has opened up via manual Device Enrollment with a User Approved (UAMDM) enrollment status. This is a big change from how supervision previously worked, and it has a lot of implications for device management moving forward.
Overview of UAMDM and Supervision
Apple introduced UAMDM in macOS 10.13.2 High Sierra. Essentially, UAMDM is an enrollment status that limits the management capabilities of IT administrators until users approve Device Enrollment. Once user consent is given, IT can enroll the device in an MDM solution, make changes to security settings, and leverage new capabilities.
Device supervision was introduced in iOS 5, and it now extends to iPadOS and tvOS. Supervision for macOS was introduced in Catalina, but it isn’t as built out as it is on other platforms. It’s more of a marketing change than a technological one, so now anything that requires “DEP enrollment” requires “supervision.” It’s simply a change in wording.
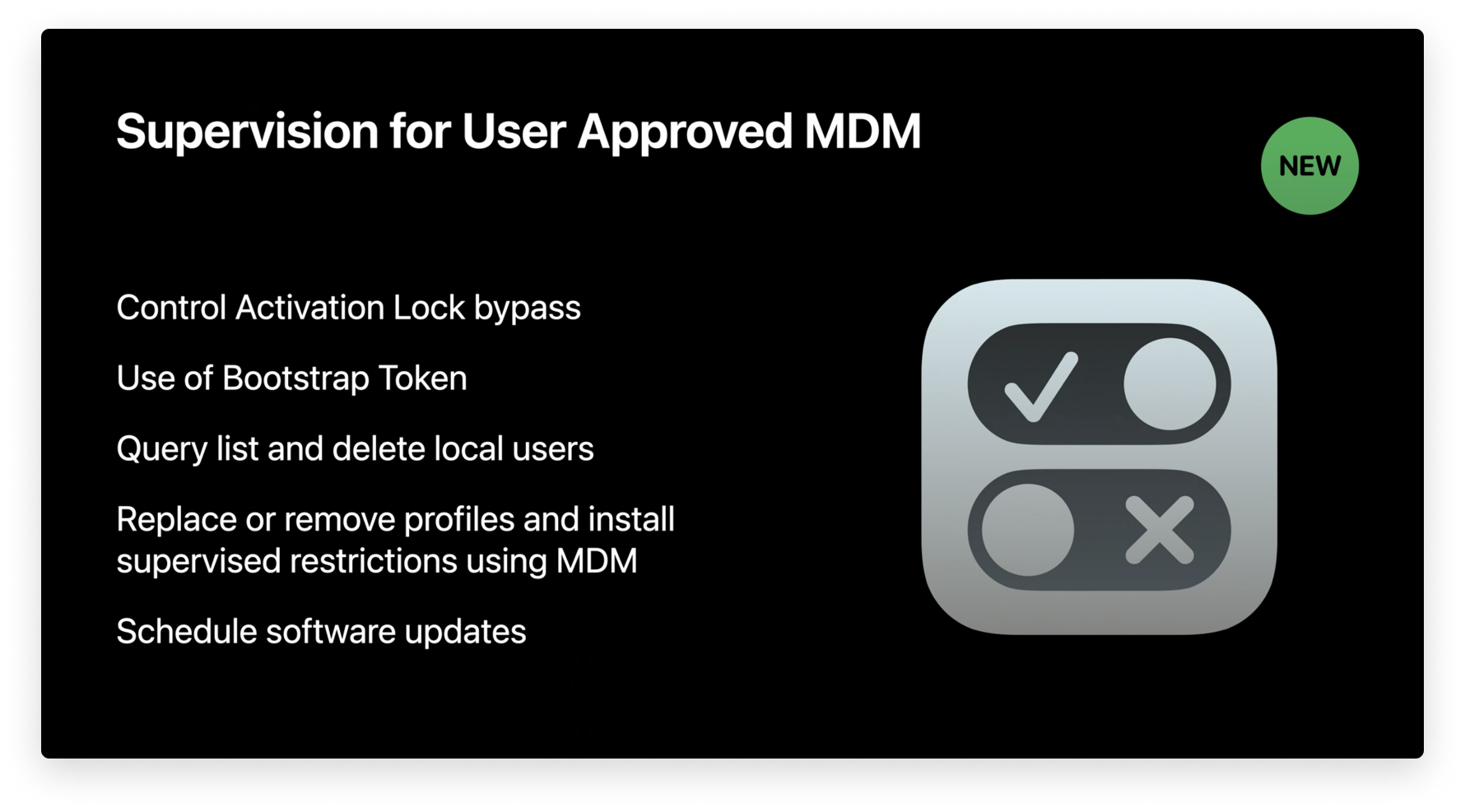
In a nutshell, supervision gives IT administrators more control over devices, letting them automate actions, add restrictions, and do things via MDM like retrieve the activation lock bypass code, retrieve a bootstrap token, delete a user, schedule an update, retrieve the user list, and more. It's important to note that some of these items like installing updates can be done via an agent instead of the MDM protocol.
While manual supervision can be achieved using Apple Configurator 2 on iOS or iPadOS, Automated Device Enrollment is the only way to achieve supervision on macOS devices. Automated Device Enrollment basically lets IT administrators configure enrollment settings for any device assigned to their MDM server – upon start-up, the device will automatically be enrolled and configured. For any device enrolled in Automated Device Enrollment, supervision is automatically enabled.
Manual Device Enrollment is a New Route to Supervision
For a quick recap, Automated Device Enrollment used to be the only way for macOS devices to be supervised, but this is no longer the case. With Apple’s most recent change, Device Enrollment with User Approved (UAMDM) status now results in device supervision on macOS Big Sur.
As a result of this change, Automated Device Enrollment (DEP) and supervision are no longer inherently the same. Since Automated Device Enrollment used to be the only way to achieve supervision, the capabilities available for supervised devices were exclusive to this enrollment method.
Now that those same capabilities are also available for devices enrolled via manual Device Enrollment with a User-Approved MDM enrollment status, we need to draw a line in the sand between supervision and Automated Device Enrollment. In the next section, we’re going to explore these capabilities and discuss their implications for IT administrators.
Implications for IT
Before Apple made the change to consider any device enrolled via manual Device Enrollment with a User-Approved MDM enrollment status supervised, Automated Device Enrollment and supervision were essentially the same. Because of this, any Mac enrolled via Device Enrollment with User Approved (UAMDM) status didn’t have the same capabilities as a Mac enrolled in Automated Device Enrollment.
This is no longer the case. Now, enrollment that’s User Approved enables supervision for macOS Big Sur, giving IT administrators the same capabilities that they previously had when using devices enrolled in Automated Device Enrollment.
We’ll break down some of these capabilities below:
- Bypass activation lock: On Mac computers with a T2 chip, when activation lock is enabled, the device user’s Apple ID credentials must be entered before IT can turn off Find My iPhone, erase the device, or reactivate it. This can cause issues if an employee leaves their job and IT cannot reuse their device without their credentials. With device supervision, MDM can retrieve the activation lock bypass code that IT can leverage to bypass activation lock .
- Leverage bootstrap tokens: Bootstrap tokens make it possible for mobile accounts to sign in to FileVault-enabled Mac computers, and with macOS Big Sur, bootstrap tokens will be required for software updates and KEXT (Kernel Extension) approval. The MDM protocol has been extended to support new features with bootstrap tokens for Mac computers, and device supervision gives IT the capabilities to leverage them.
- Query, list, and delete users: IT can also perform more actions on a device’s local users, such as querying, listing, or deleting them via MDM.
- Schedule software updates: Device supervision also unlocks MDM commands used to force and defer major and non-major OS updates.
Monitoring Supervision Status
For our MDM solution Kandji, we’ve made it easy to monitor the supervision status of your devices. In the Kandji web app, we’ve added a label in Device Details that lets you know if the selected device is or isn’t supervised, as pictured below.
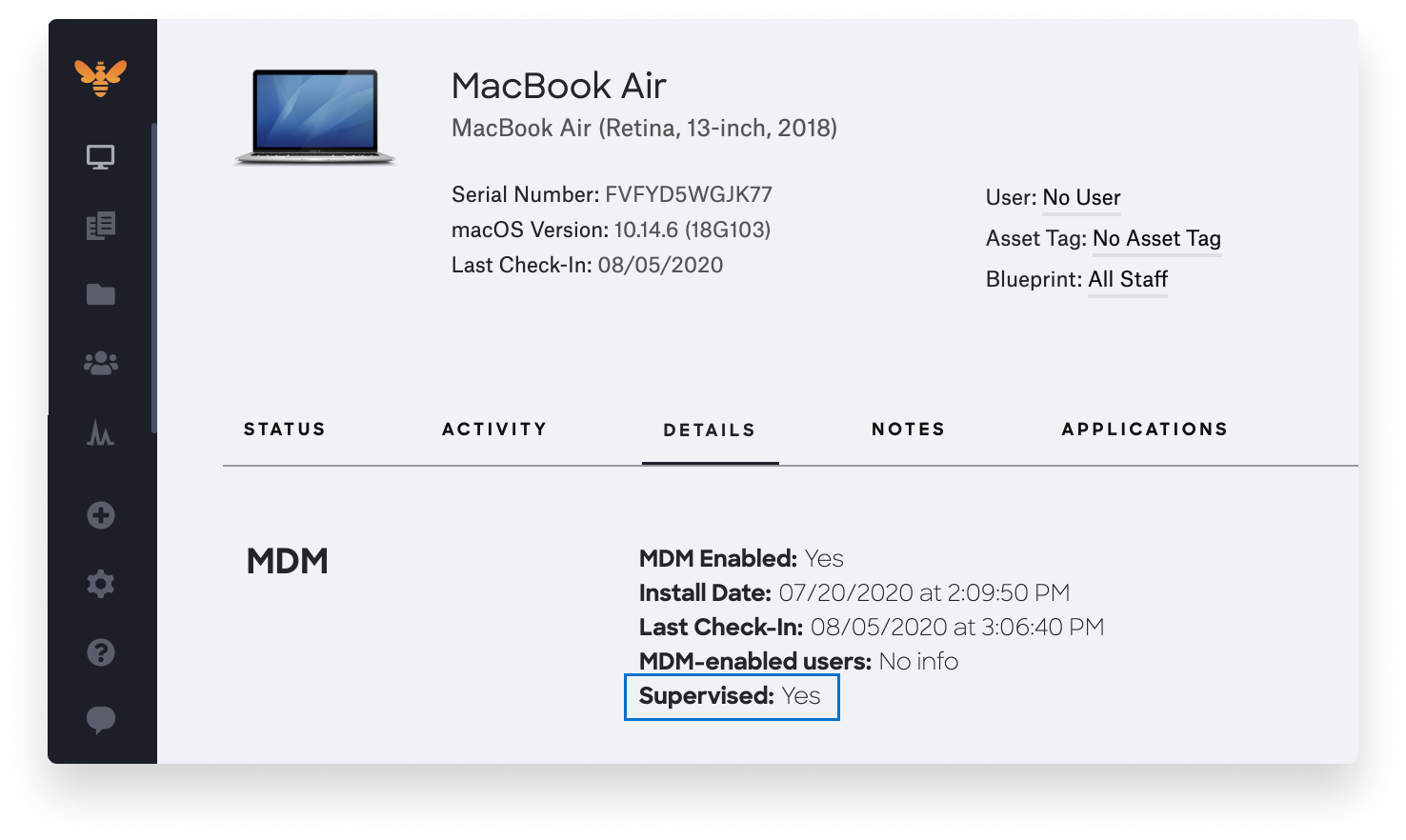
To find it, just select the device in question, go to the Details, and look at the “Supervised” field in the MDM section. It will read Yes or No.
Automated Device Enrollment is Still Important
Even though Automated Device Enrollment is no longer the only way to achieve supervision, it’s still important. In this section, we’re going to discuss a couple of reasons why.
Non-Removable MDM Profile
Let’s start with its effect on the MDM profile. By default, enrolling via Automated Device Enrollment makes the MDM profile non-removable – even for local administrators. Enrolling devices through the enrollment portal (UAMDM and Device Enrollment), however, leaves the possibility open that a tech-savvy user could remove the MDM profile. This is why we always recommend enrolling devices through Automated Device Enrollment, made possible by Apple Business Manager.
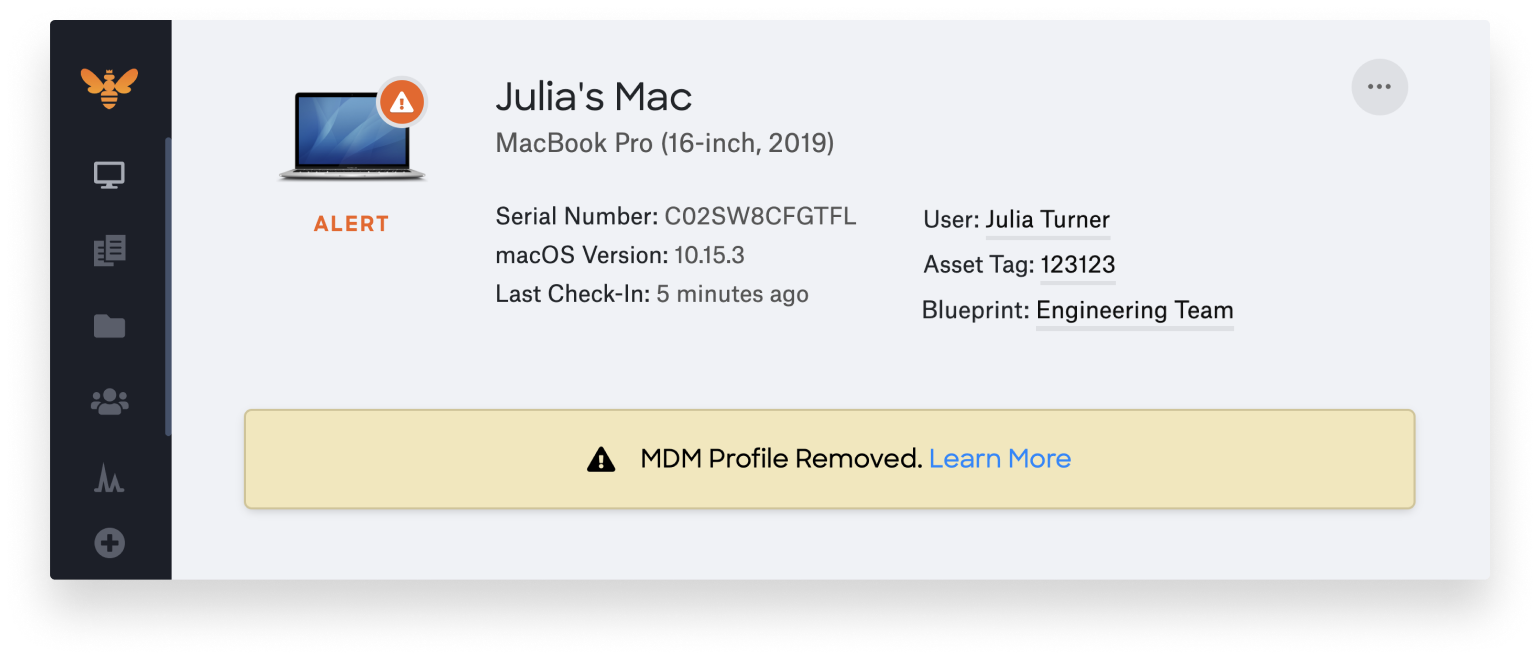
We recently updated Kandji to alert IT administrators if your users remove an MDM profile. You can see an image of the alert below. These notifications let you re-enroll devices as fast as possible.
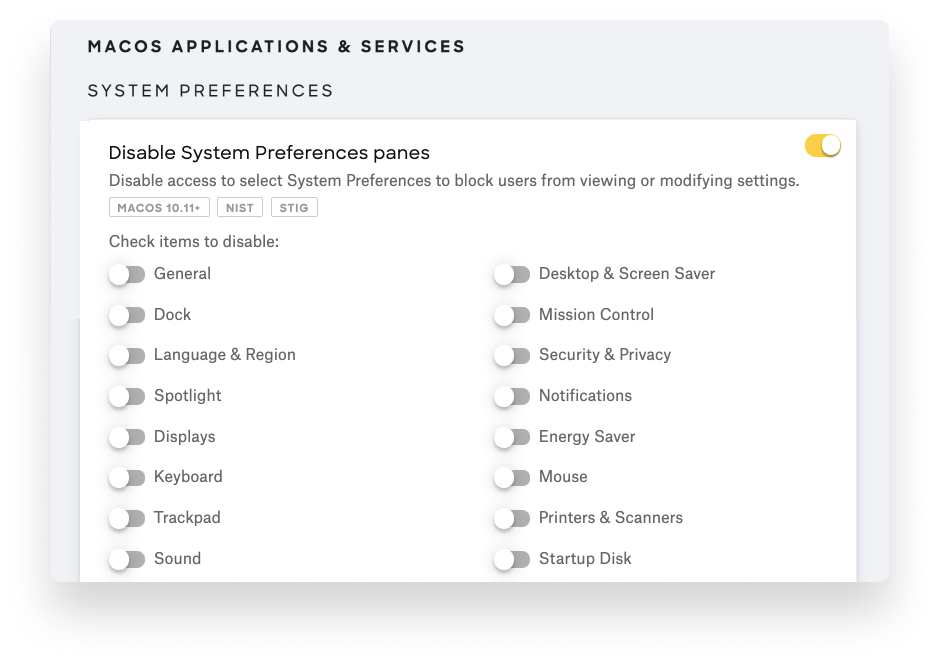
If you have to do manual enrollment, then consider using Kandji to disable sections of the Preferences pane. This will help stop users from being able to remove the MDM profile.
Auto Admin
An Auto Admin account is an MDM-configured administrator, which can only be created during the Automated Device Enrollment process. If your MDM solution doesn’t automatically create an admin, then the first account created on the device will become the admin.
To avoid users becoming administrators, you can create an Auto Admin that IT can configure, keeping your staff as non-admins. Using Kandji, you can configure this account inside of an Auto-Enroll Library Item.
We’re excited to build more solutions into our MDM solution so you can make the most out of Apple’s newest features. With Kandji, you can be confident that your Apple fleet is in safe and secure hands from deployment to retirement.