Managed Apple IDs: How to Create with Azure AD
 Kandji Team
Kandji Team
If your business is using Microsoft Azure Active Directory (Azure AD) as your identity provider, then you can use federated authentication to connect your Azure AD instance with Apple Business Manager to create a seamless login experience for your employees.
In this post, we're going to discuss a related new feature that Apple announced, SCIM (System for Cross-domain Identity Management), which makes it easier to import users into Apple Business Manager. We'll also cover how SCIM differs from a different method called just-in-time (JIT).
What is SCIM?
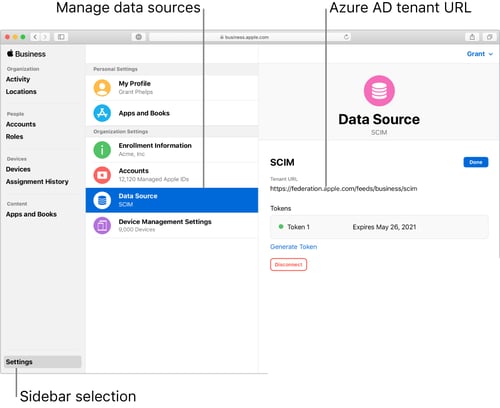 Image source: support.apple.com
Image source: support.apple.com
Apple’s recent implementation of SCIM lets IT provision and deprovision users from Azure AD in Apple Business Manager. Apple’s SCIM documentation explains that the feature merges Apple Business Manager properties with any account data imported from Azure AD.
While using the feature, the account information in Apple Business Manager is locked in read-only mode. However, once you disconnect from SCIM, the accounts can be edited manually. This includes Azure AD account roles, which defaults to “Staff,” but can be edited in Apple Business Manager once disconnected from SCIM (more information on roles here).
If you’re already using federated authentication when your Azure AD accounts are sent to Apple Business Manager, your accounts will sync from the federated domain, even though you won’t see any activity. In this case, Azure AD acts as the IdP, authenticating users for Apple Business Manager. That means any other IdPs that work with Azure AD will also work with Apple Business Manager, such as ADFS (Active Directory Federated Services).
How Does SCIM Differ from JIT?
Before SCIM was introduced, new accounts would be created as you signed into a Managed Apple ID with your Azure AD credentials. Apple Business Manager would create the account just-in-time (JIT). Accounts removed from Azure AD would not be deprovisioned from Apple Business Manager even though their credentials would stop working.
Now that Apple has introduced support for SCIM, a new path has opened up for IT, allowing you to continue using JIT or switch to this functionality. The main difference is that SCIM supports both automated provisioning from Azure AD to Apple Business Manager and automated deprovisioning.
Provisioning will automatically create new accounts as new people join your organization (sourced from your IdP), while deprovisioning will deactivate those accounts as users are removed from your organization.
How to Setup and Configure SCIM
Only users with proper permissions can enable SCIM to sync accounts to Apple Business Manager. Before you use this feature, ensure that you’re an Application Administrator, Cloud Application Administrator, Application Owner, or Global Administrator.
Note: Once you turn on provisioning, the initial Azure AD sync will begin immediately. After that, syncs will be triggered every 20 to 40 minutes.
Before you begin using SCIM, Apple recommends doing the following:
- Configure and Verify Your Domain: SCIM requires that you confirm ownership of your Azure AD domain before continuing Read our guide to domain verification to learn more.
- Configure (But Don’t Enable) Federated Authentication: Next, you'll set up Federated Authentication. Apple recommends not turning it on until all steps are completed, but you can still proceed if you’ve already enabled it.
- Determine Syncing Type: Decide if you want to sync only assigned users or sync all users. If necessary, you can create groups in Azure AD to sync specific user accounts.
- Sync Only Assigned Users: This option will only sync user accounts that appear in the Apple Business Manager Azure AD app. If you use groups, you can specify which accounts should be synced. However, keep in mind that Apple Business Manager doesn’t have a group feature, so the accounts will be independent once moved over from Azure AD.
- Sync All Users: This option doesn’t pay attention to groups. It syncs and creates Managed Apple IDs for all accounts that appear in the Azure AD User tab.
- Have an Azure AD Admin Standing By: You’ll need an Azure AD administrator with proper permissions to edit enterprise applications.
Now, you’re ready to begin using SCIM. If any issues arise, you can reference Apple’s SCIM connection troubleshooting documentation. This document covers explanations for failed SCIM connections and for incorrect Azure AD users appearing in Apple Business Manager.
From deployment to retirement, Kandji keeps your Apple devices safe and secure with a suite of features such as pre-built security settings, zero-touch deployment, one-click compliance, and much more.

