Mac Malware Persistence: What It Is, How It's Achieved
 Kandji Team
Kandji Team
When it comes to Mac malware, IT and security staff are well aware of the most common infection vectors: malicious emails or attachments, Trojanized applications, or attackers leveraging both known and unknown exploits. Apple consistently retools each version of its operating system to include better intrinsic defenses against such threats.
But as Apple devices continue to proliferate across the enterprise—in 2021, IDC found, macOS accounted for 23% of computers in use in the enterprise—attackers continue to target them. That interest has led to an increase in malware targeting Mac computers and in malware infections.
For those concerned about Mac malware, there's no better resource than Patrick Wardle. Patrick is the founder of the Objective-See Foundation and the author of The Art of Mac Malware (which is free to read online). Today, we’ll summarize some of the key points Patrick makes about one aspect of Mac malware: how it achieves a persistent presence on the Mac computers it infects.
What Is Malware Persistence?
Persistence refers to various ways that malware tries to maintain access to a system. Persistence allows malware to relaunch itself automatically following a predetermined event, such as a device startup, user login, or other events that malware ‘listens’ for.
Persistence ensures that malware will continue to operate regardless of user operations. For instance, a system restart will not affect malware that has achieved persistence; that malware will automatically relaunch when the device powers back on or the user logs in again.
Like other operating systems, macOS includes a wide variety of persistence mechanisms out of the box, to give legitimate software—such as security tools or updaters—persistence. Malware can and does abuse these mechanisms.
Most malware needs to achieve persistence to achieve its purpose, which could be anything nefarious to an organization, such as serving as a backdoor into a system or stealing passwords. If a piece of malware cannot obtain persistence, its overall impact is greatly diminished. If malware is wiped from memory and unable to relaunch after a single reboot or user logout, it’s usually not worth the effort to develop or distribute it.
That said, there are two types of threats that deliberately do not seek persistence: ransomware and highly targeted memory-only payloads. For these types of threats, persistence mechanisms are typically neither needed nor wanted by the attacker.
In the case of ransomware, persistence is unnecessary. Once an attacker has used ransomware to encrypt a user’s files and dropped its ransom note, there is no need for it to remain on the user’s system. In fact, many ransomware variants delete themselves after they have finished encrypting files, in order to make post-infection analysis more difficult.
Memory-only payloads—which, as the name implies, reside only in memory, not in storage—refrain from persistence in order to achieve higher levels of stealth on a system; however, this means they can be removed from a system by a simple device restart. These attack types are typically highly targeted and deployed by advanced actors, typically for espionage purposes.
Those exceptions aside, most attackers utilizing Mac malware seek persistence, and they leverage legitimate mechanisms built into macOS to achieve it. While there are multiple routes to achieving that persistence on a Mac, here are some of the most common.
How macOS Malware Achieves Persistence
Login Items
Login items are applications that are automatically executed when a user logs in. Any application running as a login item will inherit the user’s permissions. When successfully employed, this method ensures that macOS will automatically execute the software each time a user logs in.
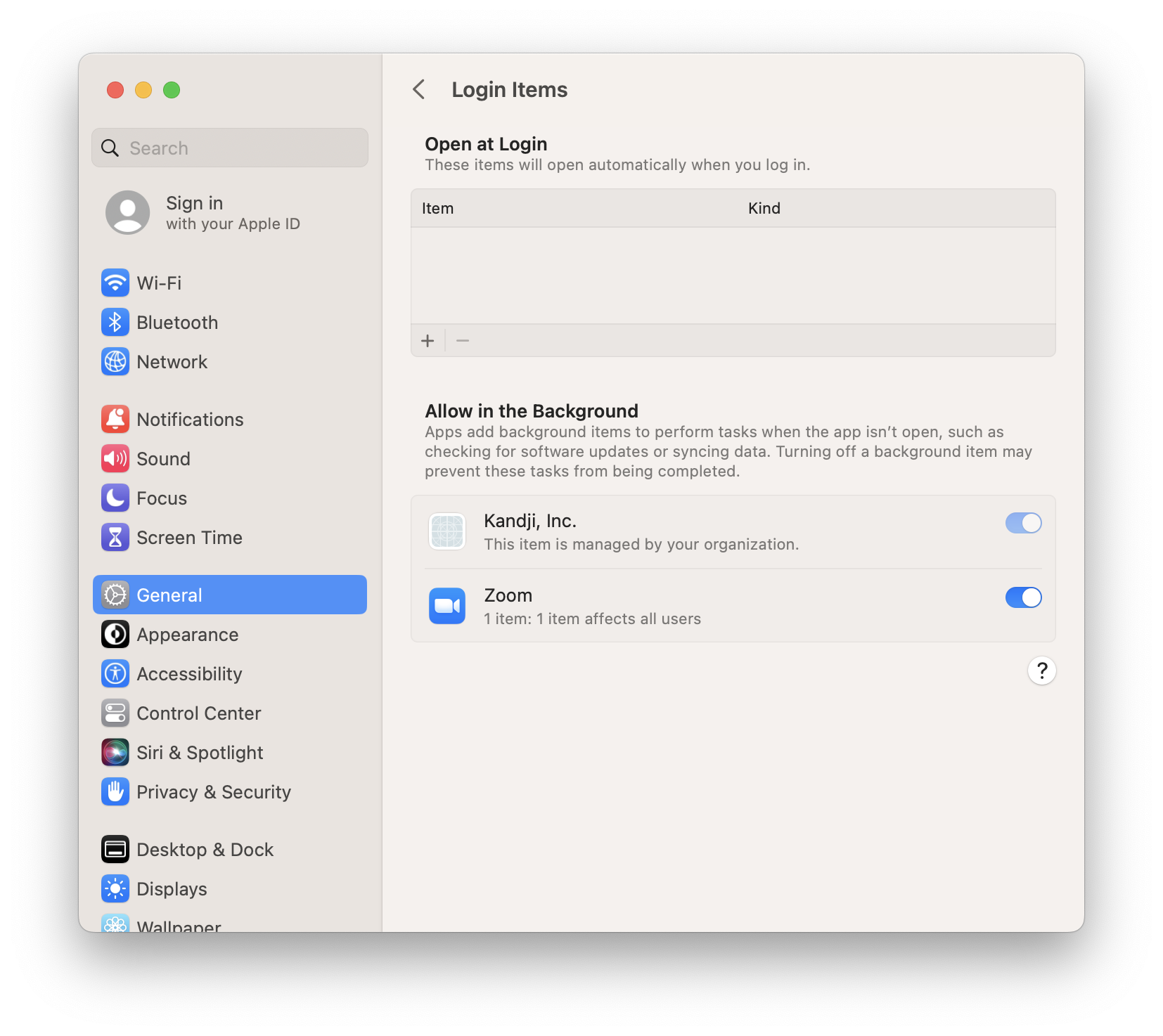
Users can find the login items associated with their profile on the Login Items tab of System Settings > General. (In versions earlier than macOS Ventura, this tab was in the Users & Groups preference pane.) It’s possible that malware may masquerade as a legitimate application.
In versions of macOS starting with 10.6.6 and later, malware could add an additional level of subversion by installing a helper login item, which does not appear in the Login Items tab.
Launch Items
Launch items function similarly to login items. But while login items provide persistence for user-visible applications, launch items can provide persistence for all kinds of binaries. Attackers using malware will attempt to gain persistence via launch items because that provides access for background processes. According to a list of emergent Mac malware from 2021 compiled by Patrick Wardle, for instance, every new malware variant discovered that year tried to achieve persistence via launch items.
There are two types of launch items malware can exploit: launch agents and launch daemons. The main difference is that launch daemons are typically launched with root privileges at system startup, while launch agents launch with user-level privileges during user login.
Lists of launch agents can be found at /Library/LaunchAgents or ~/Library/LaunchAgents, while launch daemons can be found at /Library/LaunchDaemons. In macOS Ventura, launch items that operate in the background are visible and can be turned on or off (as long as they aren’t managed) in the Allow in the Background section of the Login Items settings pane. Additionally, macOS Ventura notifies users when new background items are added. (For more on this, see our post “macOS Ventura: Bringing Transparency to Login and Background Items.”)
Scheduled Jobs and Tasks
macOS also features three ways to schedule jobs and tasks at predetermined intervals: cron jobs, at jobs, and periodic scripts. Although attackers can hypothetically abuse any of these three methods, known Mac malware currently leverages only cron jobs for persistence; even then, cron jobs are not a particularly common persistence mechanism.
Cron jobs differ from login and launch items as a persistence mechanism in that their persistence is tied to specific time intervals—hourly, say, or monthly—rather than to predetermined events such as user logins. Cron jobs can be scheduled via the /usr/bin/crontab utility.
Note that, in order to run commands on protected directories, crontab must be granted Full Disk Access in the Privacy & Security tab in System Settings. Cron tabs are stored as text files for each user in /private/var/at/tabs, which requires root privileges to access; /usr/bin/crontab -l will show you the cron jobs for that user.
Dynamic Libraries
Dynamic libraries (dylibs) are a less common method of obtaining persistence on Mac computers. Unlike some of the other methods, they are more difficult to detect, because abusing dylibs does not require an untrusted process to run on the system. Instead, attackers will use malware to force a legitimate, trusted program or process to load a malicious library. Typically, malware that exploits dylibs targets system processes or common user applications, such as web browsers, to achieve something like persistence; each time the process or application is run, it loads the malicious library.
There are three methods that malware can theoretically employ to link to malicious libraries:
DYLD_*environment variables;- dylib proxying; and
- dylib hijacking.
Currently, known Mac malware leverages only the first technique.
To take advantage of DYLD_* environment variables, attackers will attempt to inject a dylib into a process at load time. This technique forces a process to load the malicious library whenever it is started. However, following Apple’s introduction of the hardened runtime feature, Apple’s platform binaries or third-party applications compiled with this feature ignore DYLD_* environment variables.
The hardened runtime feature is powerful but has its limitations. It doesn't work if a user disables System Integrity Protection (SIP). Apple doesn't recommend doing so, but some users disable SIP for specific purposes. Additionally, potentially malicious library injection is possible if an application is entitled to com.apple.security.cs.allow-dyld-environment-variables and com.apple.security.cs.disable-library-validation.
In dylib proxying, a malicious library replaces the legitimate library that a process depends upon, and then proxies the original library for required functionality. This ensures the target process will load and execute the malicious dylib every time it is run while keeping the target process stable. Dylib hijacking is similar to dylib proxying; it can exploit programs that load dylibs from multiple writable locations.
Plugins
Third-party plugins allow for extending an application's functionality. However, plugins from untrusted sources can be loaded with malware or adware functionality. Web browsers are a particularly common target of malicious plugin-ins, which then allow for things like password stealing or traffic hijacking. Plugins achieve persistence by running each time the affected program is started.
Persistence and Mac Malware
There are a number of other persistence mechanisms available to bad actors (such as achieving persistence higher up in the supply chain). But the techniques listed above are the ones that anyone tasked with securing macOS devices should be most concerned about. Admins can go far in improving an organization's security posture by understanding the use of malware persistence as a tactic for achieving entry into that organization’s environment.
Malware, as you may have concluded, is a deep and nuanced topic; malicious software can use many tactics and mechanisms to achieve entry into an organization’s security defenses. For more details, we direct you to Patrick Wardle's book; for an update on how malware has been evolving on Apple platforms most recently, see his report "The Mac Malware of 2022."
Kandji can help IT and security admins protect against Mac malware across the entire organization. For more on that, see our recent announcement, “Kandji Announces New Device Harmony Platform” as well as our post “Guide for Apple IT: Mercenary Spyware and Lockdown Mode.”
