Guide for Apple IT: Managing FileVault
 Kandji Team
Kandji Team
Securing sensitive company data is one of the top priorities for any IT department. For businesses that run on Apple, FileVault is an essential tool for Mac security. By encrypting all of the information on a Mac computer’s startup disk, FileVault makes company information unreadable to unauthorized users.
In this article, we’ll review what FileVault is and how it can be used to secure Mac computers. We'll then discuss how admins can deploy it and also manage FileVault recovery keys.
What Does FileVault Do?
First to the review: Built into the Mac operating system, FileVault encrypts all data on Mac startup disks, allowing that data to be accessed only after proper login credentials have been entered. FileVault encrypts data in the background, so employees may not even know it’s happening, and they can use their devices while encryption is taking place.
FileVault has been a part of the Mac operating system since the release of Mac OS X Panther (10.3) in 2005. Its earliest versions were limited in scope: It could only encrypt a user’s home folder, leaving the rest of the data stored on the device's disk unprotected.
MacOS Full-Disk Encryption
With Mac OS X Lion (10.7) Apple released FileVault 2 which (thanks to the introduction of the Core Storage volume format) encrypted the entire startup disk—still without interrupting users. It was also a step up in strength, using XTS-AES-128 encryption with a 256-bit key. All that was long ago, and FileVault 2 is now known simply as FileVault.
Its implementation has continued to evolve, strengthened by security enhancements in Apple File System (APFS) and the introduction of the Apple T2 Security Chip and Apple silicon. That new hardware included always-on encryption tied to the specific device; FileVault is layered on top of that by requiring specific user credentials.
Most significantly for admins though, FileVault can be deployed and managed centrally by an IT department using MDM.
How to Enable FileVault
Turning on FileVault disk encryption is a great way for admins to prevent unauthorized access to company data on user devices, which makes it an important component of any defense-in-depth security strategy. It can be complemented by other security measures, such as requiring users to log back into their devices whenever a device wakes from sleep mode or leaves the screen saver.
With FileVault on, only FileVault-enabled users can log in after a restart; anyone else will have to wait until the disk has been unlocked by a FileVault-enabled user. While users turn FileVault on via System Settings, IT teams can use an MDM solution such as Kandji to deploy, monitor, and manage FileVault on managed macOS devices.
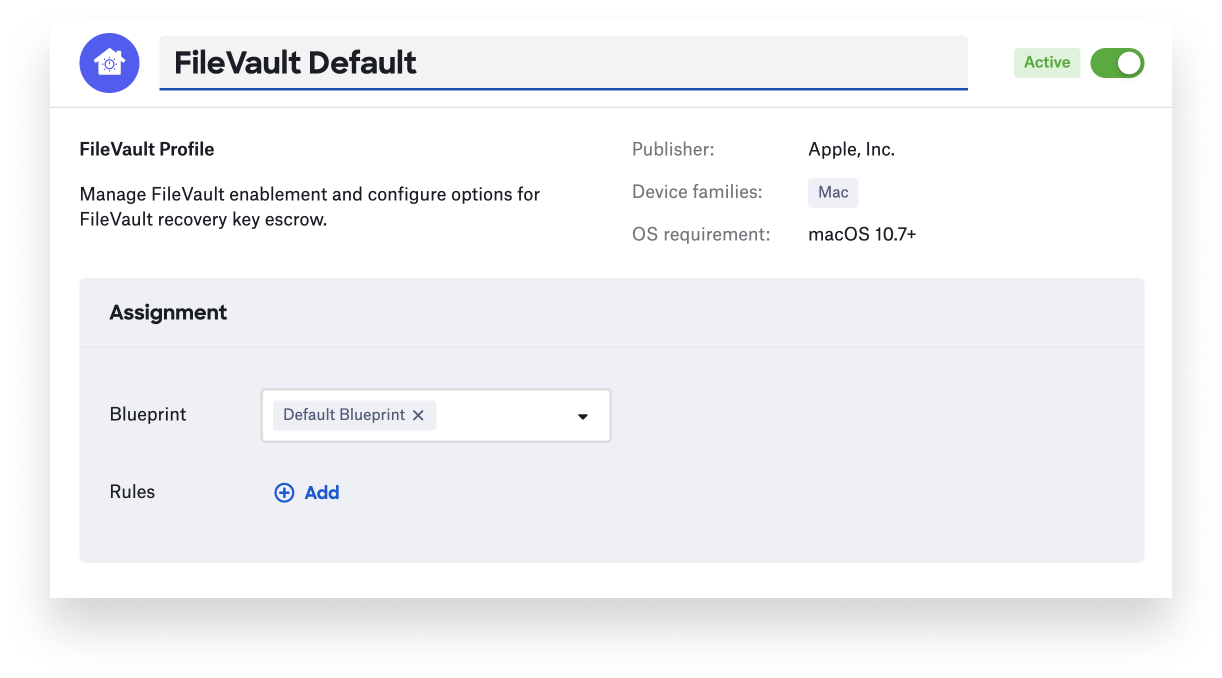
Using Kandji as an example, you can add a FileVault library item to a Blueprint. When enabled, that item will apply your chosen FileVault settings to every device in that Blueprint. You can configure it to be immediately enforced at the next login or allow the user to defer. You can also specify whether the Mac should be forcibly restarted or remind the user to restart to initiate FileVault encryption. Such an enforced restart is made possible by the Kandji Agent working together with the Kandji server.
Because booting a Mac with FileVault requires authorized user credentials, it’s not recommended to be used on Mac computers that are shared among a set of unknown multiple users, such as in a computer lab or kiosk. However, while each organization’s requirements will differ, the always-on nature of the hardware-based full-disk encryption on Mac computers with T2 chips and those with Apple silicon is often sufficient to meet the security requirements that are commonly recommended for those use cases.
How to Manage FileVault Recovery Keys
Two important considerations in managing FileVault in an organization: Deciding who will have access to the recovery key for a computer and where that key will be stored. If a user forgets their login credentials and cannot access their computer, without that key no one can log in, and the files and settings on the computer will be inaccessible.
On an unmanaged computer, when a user enables FileVault 2, they’re given two options for what to do if they forget a password: Unlock using an iCloud account and password or unlock using a FileVault recovery key (sometimes referred to as a personal recovery key, or PRK). If they choose the FileVault recovery key option, they must keep a copy of that key securely stored somewhere (not on the encrypted startup disk). In enterprise settings, the FileVault recovery key option is best, and you can enable it using an MDM solution like Kandji.
Personal Recovery Key
Despite its name, the FileVault Personal Recovery Key, or PRK, is actually anything but. Apple Platform Deployment recommends organizations use PRKs because they provide “an extremely robust recovery and operating system access mechanism” along with ensuring “unique encryption per volume.” They also offer the ability to escrow (securely store) the key with MDM, hide it from the user, and rotate it at any time; Kandji supports all of these capabilities.
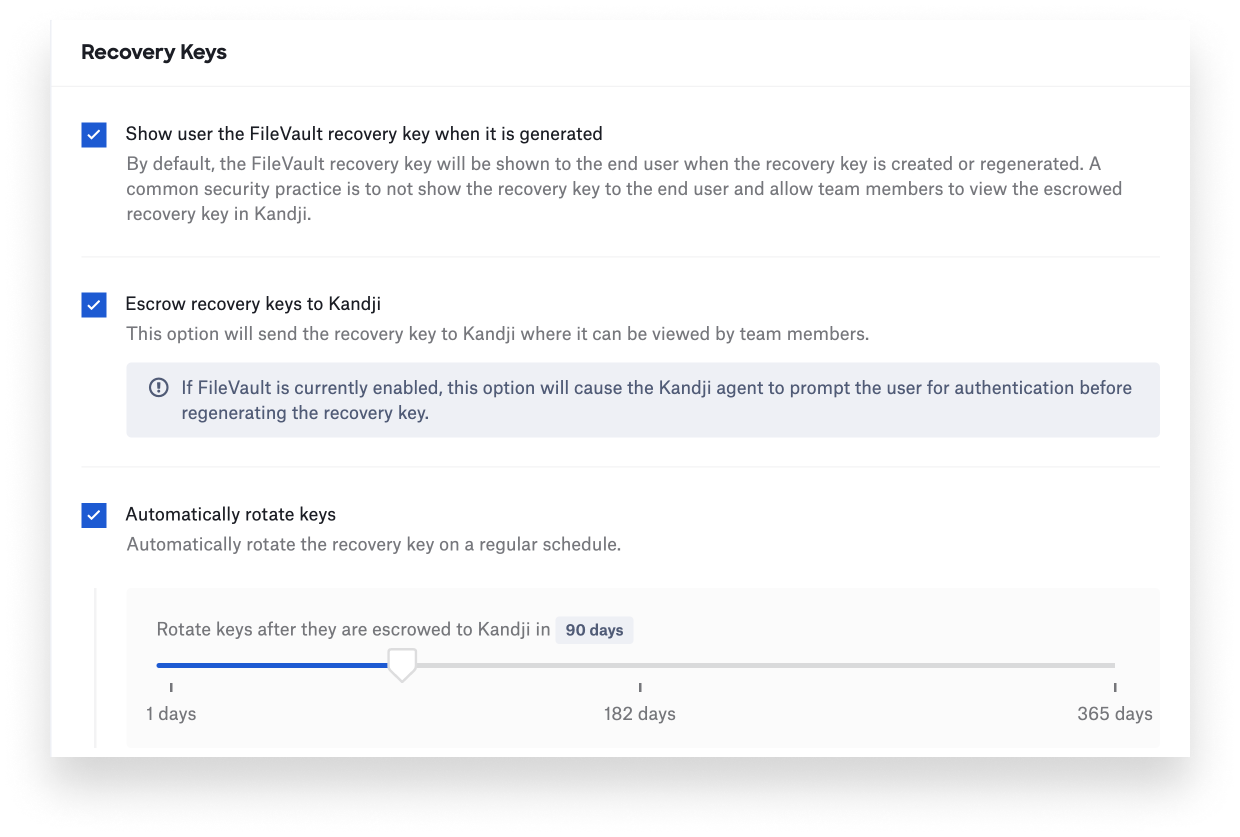 If you do escrow the key, you can use it to boot a Mac directly without needing a user’s password; you can always provide it to a user when needed, such as using recoveryOS to reset a forgotten password.
If you do escrow the key, you can use it to boot a Mac directly without needing a user’s password; you can always provide it to a user when needed, such as using recoveryOS to reset a forgotten password.
Kandji also has a built-in option for regenerating recovery keys when they are unknown, such as when migrating devices and enrolling them for the first time. If you enroll a Mac that has already been encrypted, Kandji can rotate and escrow a new recovery key by automatically prompting the user to create a new one. See our support article for more on this feature.
Note that FileVault can only be enabled by a user with a SecureToken, or if no users on the Mac currently have one. For more information on SecureTokens, including what they are and when they are issued, as well as information on the Bootstrap Token which can help grant them, please see Apple Platform Deployment. The Bootstrap Token is fully supported in Kandji.
Institutional Recovery Key
Institutional recovery keys, or IRKs, are no longer recommended by Apple for use as they provide no functional use on Mac computers with Apple silicon. For more information, see the “Institutional versus personal recovery keys” section of Apple Platform Deployment.
Editor's Note: This post was substantially revised from a previous version January 31, 2023.
About Kandji
Kandji makes it easy to manage FileVault and other crucial security settings across your entire Mac fleet. The Kandji team is constantly working on solutions to streamline your workflow and secure all of your Apple devices. With powerful and time-saving features such as zero-touch deployment, one-click compliance templates, and plenty more, Kandji has everything you need to bring your Apple fleet into the modern workplace.

