Federated Authentication in Apple Business Manager
 Kandji Team
Kandji Team
If your business is using Microsoft Azure Active Directory (Azure AD) or Google Workspace as your identity provider (IdP), then you can use federated authentication to connect your instance with Apple Business Manager. This is a great way to create a consistent, seamless login experience for your employees.
In this guide, we’ll take a closer look at what federated authentication is, how to set it up, and what it can do for you.
A quick overview of what we’ll cover:
- How does federated authentication work?
- Can I use other IdPs for federated authentication?
- What is SCIM?
- How to set up federated authentication.
- Resolving federated authentication conflicts.
- Using Shared iPad with federated authentication.
How Federated Authentication with Apple Business Manager Works
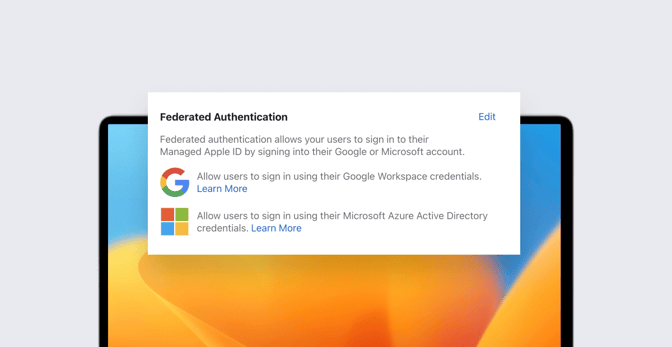
Using federated authentication lets you link your company’s Apple Business Manager account to Azure AD or Google Workspace. This allows your employees to use their existing IdP login credentials as Managed Apple IDs. They can use those IDs to sign in to Apple products and services, including Mac computers and Shared iPad devices.
In this way, federated authentication simplifies the login process for employees. Rather than having to remember multiple sets of login credentials, employees need only remember the credentials for their Azure AD or Google accounts.
Azure AD is a cloud-based directory and identity management service from Microsoft; it’s the authentication platform behind Microsoft 365. Starting with macOS Catalina 10.15, organizations can federate by connecting their instance of Azure AD to Apple Business Manager.
Google Workspace offers similar cloud-based identity-management tools as Azure AD. As of macOS 12.4 (Monterey), IT teams can link to Google Workspace using federated authentication to allow users to sign in with their Google Workspace account credentials.
These integrations let IT departments automate the creation of Managed Apple IDs at scale during the enrollment process. In most cases, when you use federated authentication, Azure AD or Google Workspace will play the part of the identity provider (IdP)—the platform that stores and manages login credentials and controls authentication to a service provider that end-users are accessing. In this case, the service provider is Apple Business Manager.
With federated authentication, these credentials are passed from Azure AD or Google Workspace to your company’s Apple Business Manager account via Security Assertion Markup Language (SAML). That then seamlessly creates Managed Apple IDs in Apple Business Manager for your employees.
This automated, just-in-time (JIT) account creation is the heart of federated authentication. By letting employees access Apple services using their existing IdP credentials, you streamline their login experience. And since that login experience integrates into the device setup process, admins won’t have to manually create accounts and users won’t have to log in multiple times.
It’s also important to mention Apple’s domain verification requirements. We’ll cover this more in a bit, but for now just know that whenever a Managed Apple ID is created, you have to prove that your organization owns the domain. In some cases, initiating federation and claiming domains can lead to conflicts. We’ll discuss how you can resolve these a little later.
For employees to access their Managed Apple IDs, they are directed to the Azure or Google sign-in page to enter their company credentials, and that authorization is passed back to Apple.
Can I Use Other IdPs for Federated Authentication?
You can do federated authentication with other IdPs as long as yours works with Azure AD or Google Workspace. While you can’t federate Apple Business Manager directly with IdPs like Okta or OneLogin, you can create and integrate Azure AD with those IdPs, and then federate Azure AD with Apple Business Manager.
So, for example, if you sync Azure AD with your OneLogin Directory, you can use your OneLogin credentials with Apple Business Manager. Since Azure AD is free for up to 500,000 objects, this is a feasible plan for organizations that rely on other IdPs. However, while this works well for some IdPs, it can be more complicated for others.
What Is SCIM?
Apple’s implementation of SCIM (System for Cross-domain Identity Management) lets IT admins provision and deprovision users from Azure AD in Apple Business Manager. It is applicable to Azure AD only. Apple’s SCIM documentation explains that the feature merges Apple Business Manager properties with any account data imported from Azure AD.
While using the feature, the account information in Apple Business Manager is locked in read-only mode. However, once you disconnect from SCIM, the accounts can be edited manually. This includes Azure AD account roles (which default to Staff); they can be edited in Apple Business Manager once disconnected from SCIM.
If you’re already using federated authentication when your Azure AD accounts are sent to Apple Business Manager, your accounts will sync from the federated domain, even though you won’t see any activity. In this case, Azure AD acts as the IdP, authenticating users for Apple Business Manager.
Before SCIM was introduced, new accounts would be created as you signed into a Managed Apple ID with your Azure AD credentials. Once Apple introduced support for SCIM, a new path opened up, allowing IT teams to continue using JIT or switch to SCIM. The main difference is that SCIM supports automated provisioning from Azure AD to Apple Business Manager as well as automated deprovisioning.
Provisioning will automatically create new accounts as new people join your organization (sourced from your IdP). Deprovisioning will deactivate those accounts as users are removed from your organization. For more on this, see our guide to creating Managed Apple IDs.
How to Configure Federated Authentication in Apple Business Manager
If you want to turn on and test federated authentication, there are three main steps:
- Add and verify a domain. Federated authentication requires you to confirm ownership of your Azure AD or Google Workspace domain. Doing so ensures that your organization has the authority to modify the domain name service records. (For more information on this, you can read Kandji's support article on domain verification.)
- Set up Apple Business Manager federation. This involves connecting Apple Business Manager to your instance of Azure AD or Google Workspace. By configuring federated authentication, you ensure that the IdP trusts Apple Business Manager and has permission to send relevant information.
- Test authentication. Once you’ve verified your domain and configured federated authentication, you can begin testing it with an IdP account. If the test is successful, you can create additional accounts and continue federating your domain.
Once you’ve verified your domain, the next step is to configure the Apple Business Manager federation process. This will let you connect Apple Business Manager to your instance of Azure AD or Google Workspace.
The gist of what that entails: When you’re signed in to Apple Business Manager (with the role of either Administrator or People Manager), go to Preferences > Accounts, click Edit in the Federated Authentication section, select your IdP, then Connect. Enter your account credentials, then proceed through the application agreement and consent forms. When you’re done with all that, click Done.
If you run into any problems in this process, double-check to be sure that the username and password combination you entered is correct. If you’re still having issues, you may not have sufficient privileges.
How to Test Federated Authentication in Apple Business Manager
If you were able to successfully configure Apple Business Manager federated authentication, then you’re ready to test it. Here’s how:
First, turn on federated authentication. To do so, sign in to Apple Business Manager with an account that has the role of Administrator or People Manager. Select Preferences > Accounts > Domains, then click Edit. Turn on federated authentication for the domains that have been successfully added to Apple Business Manager. It may take a while to update all accounts.
Once that update is complete, you can test the connection. Just make sure that you’ve successfully connected and verified your domain, and that the check for user name conflicts is complete.
Apple Business Manager: Remove Federated Authentication
If you want to disconnect federation for a domain in Apple Business Manager, you can do so in Preferences > Accounts > Domains. Depending on whether or not you’ve turned on federation, doing so will either turn it off or disconnect it. Apple has all the instructions here.
It’s important to note that you won’t be able to remove federated authentication or disconnect from a federated domain if you’re in the middle of enabling federation or resolving an Apple ID conflict. A few other things you should keep in mind when disconnecting federation:
- Users who are added in your identity provider will not automatically be pushed to Apple Business Manager.
- Users can not authenticate to federated services using their IdP credentials.
- Existing users provisioned to Apple Business Manager will remain in Apple Business Manager
- That said, existing users will not be able to use their most recent IdP passwords to authenticate to accounts associated with Apple Business Manager.
- Upon their next login, existing users will be prompted to update their existing Apple Business Manager passwords.
How to Change User Information
Once federated authentication is configured in Apple Business Manager and a link between Azure AD or Google Workspace and Apple Business Manager is established, changes to a user’s password in Azure AD will invalidate that user’s session. They will have to log back in with the new password to continue using federated authentication.
Other user details can be changed as well, including:
- email to a federated or unfederated domain;
- Managed Apple ID to a federated or unfederated domain; or
- role in Apple Business Manager.
Apple Business Manager Federated Authentication Conflicts
Conflicts can arise when you set up federated authentication in Apple Business Manager. When you set up federated authentication, Apple Business Manager checks for conflicts between existing Apple IDs and your domain name. If it finds that another user has claimed an Apple ID that contains the domain that you want to use, you can reclaim that username.
(Note that there are some significant differences between Azure AD (SCIM) and Google Workspace when it comes to resolving such conflicts.)
For instance, if your organization registered the domain @accuhive.com and a previous employee has used his business email address as a Personal Apple ID (i.e., john@accuhive.com), you cannot create a Managed Apple ID for john@accuhive.com.
Instead, Apple can notify the user that they must change their Apple ID within 60 days. If the username isn’t changed within that 60-day period, it will be automatically renamed to a temporary username, and the desired ID will be released to your organization.
When it comes to Managed Apple ID conflicts, it’s not quite as simple. If another organization uses Managed Apple IDs containing your domain, Apple will have to investigate which organization truly owns that domain. Once the investigation is complete, you will be notified, and the organization with proper ownership will claim the domain. If both organizations have a valid claim to the domain, neither can federate it.
Within Apple Business Manager, you can explore federated authentication conflicts by following the steps outlined here. Note that when you’re resolving conflicts, you can’t see the exact names of those conflicted users; this is a privacy measure.
Federation with Shared iPad
As of iPadOS 13.4, Apple introduced Shared iPad for business. Previously exclusive to education customers using Apple School Manager, Shared iPad’s new integration for Apple Business Manager let employees use their Managed Apple IDs to sign in to and recall their data on Shared iPad, achieving a true multi-user experience.
If you’re using Shared iPad and federated authentication, the sign-in process will be different than with single-user devices. For a user to sign in to their Shared iPad account when federated authentication is in use, the user will be prompted to enter their IdP credentials. The user will then be asked to create a Shared iPad passcode or password. The next time the user signs in, they will use their Azure AD username and that new passcode or password.
If the user forgets their Shared iPad passcode, an IT administrator can reset it for them in Apple Business Manager by locating the account in question and clicking the Reset Shared iPad Passcode button. However, it’s important to note that if federated authentication is configured, changing the Shared iPad passcode will not change the user’s Azure AD password. For a deeper dive into the implications, history, and deployment of this new feature, you can read our guide to Shared iPad.
Editor’s Note: This Guide was substantially updated March 2, 2023 to include coverage of the compatibility between Apple Business Manager and Google Workspace (among other changes).